The Building of an Effective & Cost-Efficient Security Plan
Did you ever stop and think: How did our security program get to the point it is at today? What was the first clue that there was a real need for some sort of security and loss prevention effort? These questions can be applied with equanimity if the security program is five years old or fifty years old. Was the security program initiated out of convention, or was it driven by need? If it was driven by need, what were the determinations that identified those needs? What are the foundational bases for determining if those needs are relevant today? If your security program looks differently than it did 10 of 20 years age, what drove those changes? Do you believe those changes, if any, were made with objectivity?
Security is a situational discipline, in part determined by the ambient threat environment. We have seen security programs that are 20 years old, that are effective with demonstrable ROI. We have also seen security program using all the contemporary technology, that are marginal at best. If the purveyors of technology know more about what they are selling, then the buyers know about what they are buying, the outcomes are not always good.
The best security programs are driven by data provided by computer-based security management systems. This technology, which gets better every year, has been around for about 20 years. This technology helps to effective security programs effective moving forward.
Not only have security management systems gotten better and more sensitive, so has security technology. In fact, security technology has not only gotten better, it has become more economical. Compare the low-light video camera of 20 years ago with the cameras currently on the market. Not only has technology improved, but because of sophisticated security technology, there is less reliance on payroll burden.
Moving forward, the first step in process should be a comprehensive security assessment. One needs to know where they have been, before determining where they are, going forward.
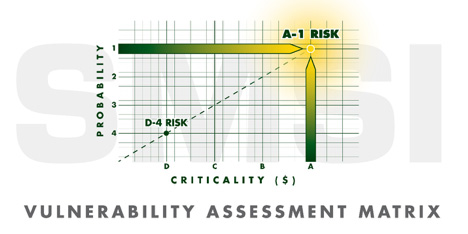
Please note that the Vulnerability Assessment Matrix defines risks as being two dimensional. Those dimensions are Probability (What are the chances that an identified risk will occur) and Criticality (What are the costs, both direct and indirect, should the identified risk come to fruition). In other words, beyond the mere identification of risk factors, cost and probability must be part of the calculus.
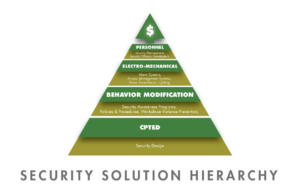
Once the security assessment has been completed, the next step requires the application of, need driven, mitigation strategies. The function of the Security Solution Hierarchy model is to provide a cost-effective construction for a security plan that works. The Security Solution Hierarchy provides a sequential roadmap for a wide range of solutions, as cost effectively as reasonably possible. Depending of the enterprise being protected, coupled with the ambient threat environment, all four levels of the hierarchy may not be required.
The first level if CPTED, because it is cost efficient, and generally, a onetime expenditure, excepting the cost of electricity for lighting. Behavior Modification includes the active participation of all employees in support of the security program. This objective requires a minimal amount of training. The Electro-Mechanical level includes the application of access control systems, including real visitor control, surveillance systems and security alarm systems. The final, and most costly level is represented by security personnel in the form of payroll burden, with is a recurring cost factor. The Security Hierarchy construct ensures a cost-efficient budgetary process. The Hierarchy also provides a level of logic for the justification of almost any Security Budget.

Please do not hesitate to contact us if you would like to discuss some of the roles your security department may be able to address pertaining to the present crisis, as well as future crisis yet to come. The application of security strategies must be applied to hospital exteriors, as the security of inner space. Because security is always a situational discipline, security programs must be designed to mitigate the threats of a dynamic, ever changing, threat environment. This includes the use of security technology supported by well-trained security personnel.
If you require further information, and/or, would like to request a security assessment for your hospital, our contact information is listed below. We would welcome the opportunity to submit a comprehensive Proposal for your consideration.
