The concept of Security Management Support (SMS) is an idea whose time has come. Not all security operations require a fulltime, credentialed security manager. However, most security operations require professional expertise from time to time. As security experts, we are frequently called upon to testify in security-driven litigations where the primary complaint is inadequate security. These cases have involved hospitals, shopping malls, industrial sites, the lodging industry, and sports and entertainment venues, to name a view. These cases are largely characterized as crimes against property and crimes against persons.
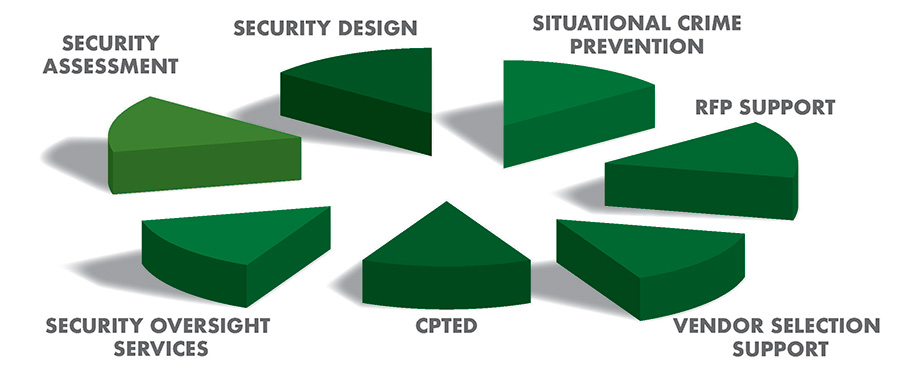
Therefore, security should be an anticipatory discipline with the goal of prevention. Security must also be a dynamic discipline, able to adjust to nuance changes to the threat environment, both internal and external. The graphic above is intended to provide a representation of the range of potential benefits to be derived from our team.
The Security Management Support (SMS) concept recognizes the real need for a diversity of skill sets essential to building and maintaining a cost-efficient and effective security operation. The SMS model also acknowledges the potential key role that security design should play. Remember, security is a proactive discipline. This means that dynamic security programs must reasonably anticipate and mitigate a wide range of ever-evolving threats. Threat mitigation also continues to draw the attention of State and Federal regulatory agencies such as OSHA. Additionally, tort law continues to redefine reasonable standards of care for specific industries.
SMS is particularly well-suited to enterprises that cater to and are accessible to the public such as Hospitals, Shopping Malls, Educational Facilities and the Lodging Industry. In part, the Security Management Support approach acknowledges that every employee should be trained to be part of the solution.
Security Needs Assessment
Because security is a situational discipline, every security program is distinct and unique, predicated on a set of specific needs. This uniqueness is defined by a number of cultural and sociological factors, which produces a unique crime pattern milieu. Therefore, the first step in the process, would be to conduct a comprehensive security assessment. Therefore, the first step of the Security Management Support process is to determine the unique security needs of each client. This entails gaining an understanding as to where the security program has been, where it is now, and where it needs to go moving forward. The assessment processes are quantitative exercises.
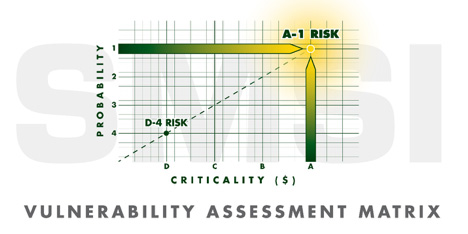
This process requires a quantitative evaluation of the risk environment. As depicted above, the Vulnerability Matrix is unique for each entity. The reasonable standard of  care model differs from one industry to another in terms of intensity. Additionally, all identified risk factors must be quantified as two dimensional: criticality and probability. Criticality is defined by the financial impact should the identified risk come to fruition. Probability is quantified by the statistical data that defines the likelihood that an identified risk will come to fruition.
care model differs from one industry to another in terms of intensity. Additionally, all identified risk factors must be quantified as two dimensional: criticality and probability. Criticality is defined by the financial impact should the identified risk come to fruition. Probability is quantified by the statistical data that defines the likelihood that an identified risk will come to fruition.
Given the ambient threat environment, security programs should be designed for reasonable prevention. Part of the quantification process will be derived by the application of a CAP Index Crimecast Report. All too often security programs are assessed after-the fact through the process of litigation. Our team is frequently called upon to be retained for security litigation cases, after-the-fact.
Effective security programs must not be built on speculation and unsubstantiated assumptions. They should be the product of real data. Data should also be the backbone of the security program going forward.
The more we can quantify the threat environment, both internal and external, the more we craft a meaningful and effective security program. The graphic above illustrates some of the services provided under a SMS model. The most effective security programs properly use a combination of remedial strategies such as: CPTED, video surveillance, access management systems, alarm systems and contract guard services, along with a well-qualified security management team. The SMS approach supports the notion the “The Whole is Greater than the Sum of the Parts.” SMS also ensures this approach is cost efficient. The SMS team will qualify and support the security vendors selection process, including the drafting of RFPs, and selection oversight.
SMSI continues to be retained as expert witnesses on numerous occasions. These cases include, but are not limited to:
- Healthcare Facilities

- Educational Facilities
- Shopping Malls
- Residential Complexes
- Entertainment Venues
- Sporting Event Venues
- The Lodging Industry
- Industrial Complexes
- Public Utility Sites
- Bars & Night Clubs
This graphic illustrates the dynamic objectives of the assessment process in support of the ongoing security support service offered herein.
Another strategy of a dynamic and effective security program is the application of Incident Reporting Software, such as provided by OMNIGO Incident Reporting Software. The use of security OMNIGO management software will enable security directors as well as the C-Suite management team TO cost effectively justify security budgets, as well as providing the SMSI Inc. Team with the information needed to ensure that your security program is always contemporary. The application of OMNIGO Software, will ensure that your security program remains relevant going forward. This software will identify emerging threat factors at the incipient stage. The difference between using OMNIGO, and not, is the difference between hunting with a rifle, as opposed to using a shotgun. Security budgets must focus on needs that are clearly identified and quantified.
Additional OMNIGO Resources (click links for downloadable PDFs):
iTrak Incident Reporting
iPass Visitor Management
iPass Kiosk Software
If it is mutually determined that added security technology should be applied, and/or the application of security personnel, SMSI Inc. will help to support the RFP process.
Crime Prevention through Environment Design
 Both Bill Nesbitt and Drew Neckar are Certified CPTED practitioners. CPTED is a frequently overlooked strategy. Ironically, CPTED is one of the most cost-efficient strategies. The application of CPTED techniques should be implemented prior to the application of higher-level budget solutions. Conversely, the lack of CPTED methodologies will decrease the potential cost benefits derived from other security strategies such as traditional physical security methodologies, including uniformed security officers.
Both Bill Nesbitt and Drew Neckar are Certified CPTED practitioners. CPTED is a frequently overlooked strategy. Ironically, CPTED is one of the most cost-efficient strategies. The application of CPTED techniques should be implemented prior to the application of higher-level budget solutions. Conversely, the lack of CPTED methodologies will decrease the potential cost benefits derived from other security strategies such as traditional physical security methodologies, including uniformed security officers.
CPTED design is strongly supported by most Police jurisdictions. Of all security methodologies, CPTED is probably the single most cost-effective security strategy.
Both Drew and Bill are Certified Protection Professionals. Both are also credentialled CPTED (Crime Prevention Through Environmental Design) practitioners. Our CVs and Letter of Terms will be provided upon request. Call 805-241-3800. Because of our extensive experience as court certified security experts, we have been able to successfully mitigate most security shortfalls.
Call or email us with any questions you may have. We welcome the opportunity to submit a comprehensive proposal for your facilities.
William H. Nesbitt, CPP
bill@smsiinc.com Call: 805/499-3800
Member:
ASIS International
IAHSS
ASHRM
ACHE
ICSC
ICA (International CPTED Assoc.)